Phishing between the App Whitelists
- 2 minsAn increasing number of organisations is moving towards virtual desktop environments. They are often easier to administer and maintain, and provide possibilities for additional security layers. One of those security layers more and more encountered at organisations is the RES One Workspace whitelisting solution. While quite a lot was written lately on bypassing AWL (Application Whitelisting), these techniques are aimed towards bypassing Microsofts AppLocker/Device Guard in Windows 10. A reasonably secure configuration of RES One Workspace blocks execution of all of these Microsoft signed binaries (InstallUtil.exe, regsvcs.exe, regasm.exe, regsvr32.exe) used to run code within their context.
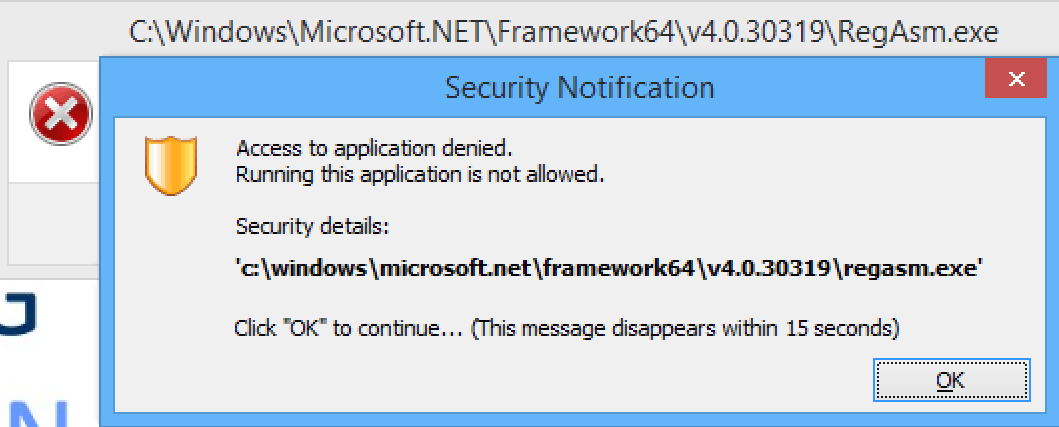
dlls blocked by RES One.RES One also becomes annoying while phishing with Empire, as the execution of the Empire stagers is prevented by RES One, blocking the execution of powershell.exe entirely for that victim user.
However, either by mistake or for the sake of keeping intact certain Windows functionality, rundll.exe is typically whitelisted by administrators. Depending on the type of pentest, rundll can be used to spawn a Command Prompt, using the ReactOS cmd.dll.
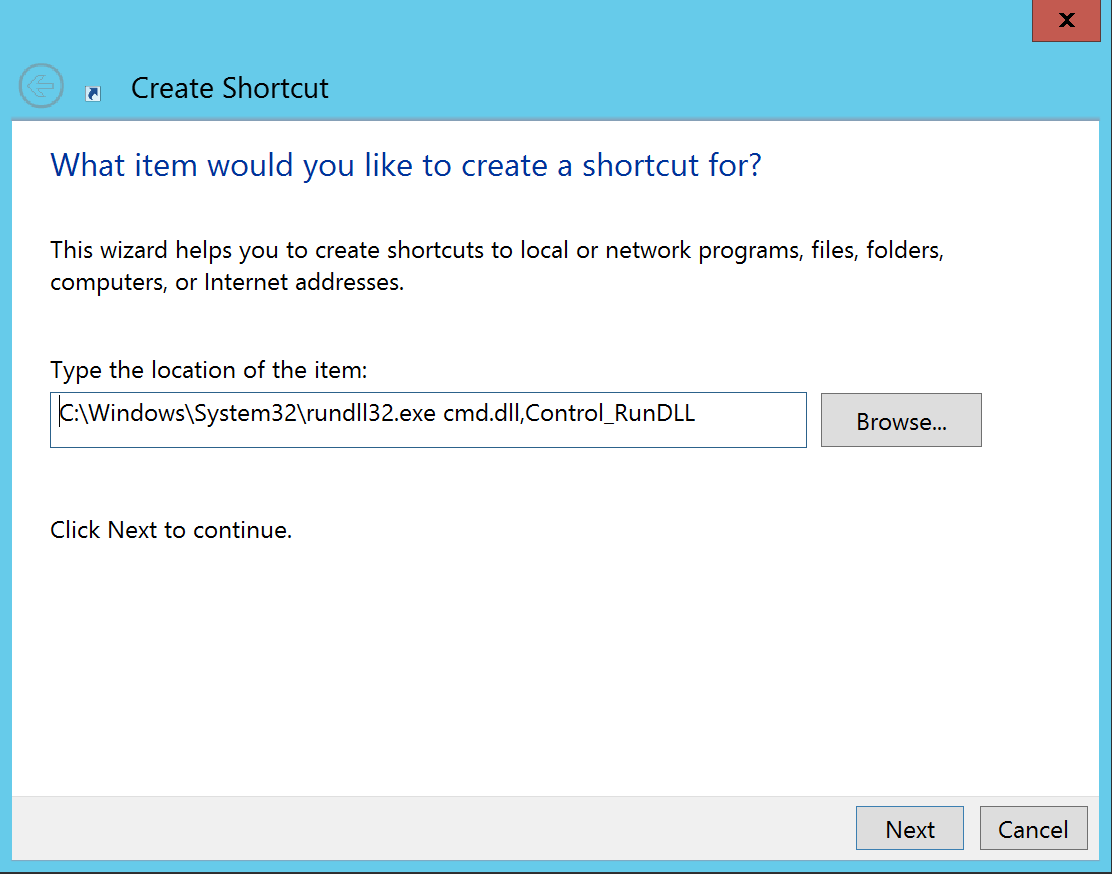
Creating the following shortcut to cmd.dll via rundll32.exe yields a pretty functional “Command Prompt”. From there it is oftentimes possible to return to your usual PowerShell environment. Recently, @xP3nt4 created the PowerSdll project which is a more functional alternative to cmd.dll.
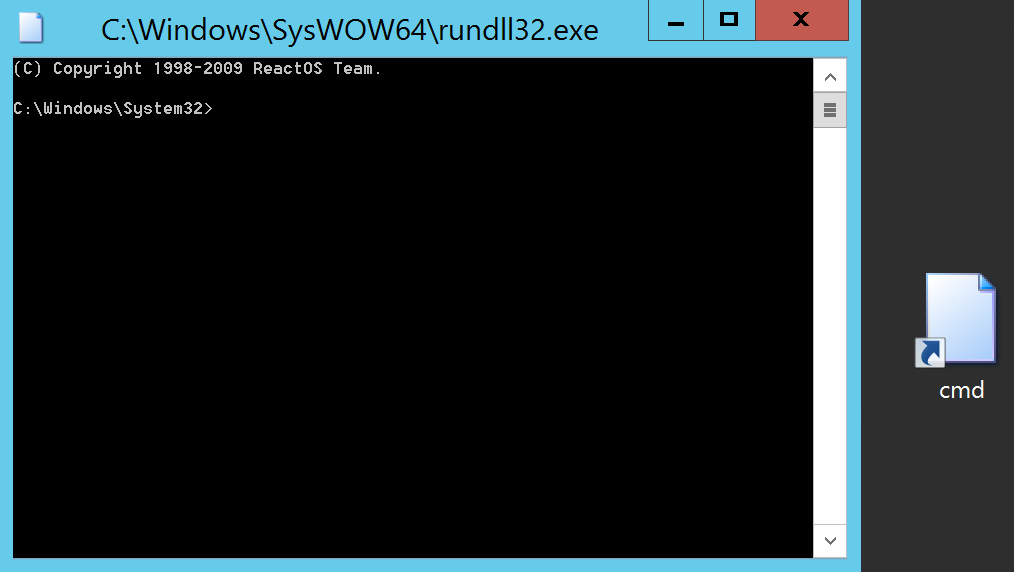
The PowerSdll project also provides a bypass for our phishing issue. We can now create a macro that downloads the PowerShdll.dll for the right architecture, and uses the downloaded dll to execute a PowerShell script (in this case an Empire stager) via rundll.
The VBA script below is a PoC I wrote that spawns an Empire agent in a RES One environment. It downloads the proper PowerShdll.dll corresponding to the system’s architecture to the user’s Temp directory and executes the script at https://127.0.0.1/Empire_default_launcher.ps1 (in this case the output of launcher ListenerName.
Running an AWL solution?
- Try to blacklist
rundll32.exe - Make sure to also include
dll'sin your AWL. An AWL only checking for executables is not really a (AWL) solution.